🎓 A full CISSP notes compilation — organized for clarity, memory, and exam prep efficiency.
Table of Contents
Open Table of Contents
- CIA
- ✅ CISSP Domain 1 – Security and Risk Management (Simple Notes)
- CISSP Domain 2: Asset Security
- Domain 3: Security Architecture and Engineering
- Biba Model
- Brewer-Nash Model
- Clark-Wilson Security Model
- Graham-Denning Security Model
- Encryption
- Definitions:
- Summary of Key Topics:
- Main Points:
- Caesar Cipher
- Encoding and Decoding
- Transposition in Cryptography
- Confusion
- Diffusion
- Key Clustering
- Synchronous and Asynchronous in Cryptography
- 1. Synchronous (Symmetric) Encryption:
- 2. Asynchronous (Asymmetric) Encryption:
- 1. Certificate Authority (CA)
- 2. Registration Authority (RA)
- 3. Work Factor in Cryptography
- 4. Methods of Cryptography
- 5. Initialization Vector (IV)
- 6. One-Time Pad
- 7. Steganography
- 8. ECB vs. CBC (Modes of Block Cipher)
- Stream vs. Block Ciphers:
- Block Cipher Modes of Operation:
- 1. CFB (Cipher Feedback Mode):
- 2. OFB (Output Feedback Mode):
- 3. CTR (Counter Mode):
- Cryptography Algorithms: Quick and Easy Notes
- 1. Data Encryption Standard (DES)
- 2. AES (Advanced Encryption Standard)
- 3. SAFER (Secure and Fast Encryption Routine)
- 4. RSA (Rivest-Shamir-Adleman)
- 5. Diffie-Hellman Algorithm
- 6. ElGamal Algorithm
- 7. ECC (Elliptic Curve Cryptography)
- 8. Birthday Paradox/Birthday Attack
- Domain 4: Communication and Network Security
- OSI Layers (Open Systems Interconnection Model)
- CSMA (Carrier Sense Multiple Access)
- Ethernet (IEEE 802.3)
- ADSL (Asymmetric Digital Subscriber Line)
- RADSL (Rate-Adaptive Digital Subscriber Line)
- VDSL (Very High Bitrate Digital Subscriber Line)
- → ARP (Address Resolution Protocol)
- → MPLS (Multiprotocol Label Switching)
- ICMP (Internet Control Message Protocol)
- IGMP (Internet Group Management Protocol)
- OSPF (Open Shortest Path First)
- SNMP (Simple Network Management Protocol)
- LDAP (Lightweight Directory Access Protocol)
- SDN (Software-Defined Networking)
- CDN (Content Delivery Network)
- PAT (Port Address Translation)
- SIP (Session Initiation Protocol)
- IRC (Internet Relay Chat)
- Domain 5: Identity and Access Management
- Centralized vs. Decentralized vs. Hybrid
- Access Control Management
- Physical Access Control Systems (PACS)
- Access Control Token
- Provisioning and Deprovisioning
- Biometrics
- FIM (Federated Identity Management)
- SAML (Security Assertion Markup Language)
- OAuth (Open Authorization)
- OpenID
- LDAP (Lightweight Directory Access Protocol)
- Types of Access Control
- Accountability in Identity and Access Management (IAM)
- Domain 6: Security Assessment and Testing
- 🧪 1. What Is Security Assessment & Testing?
- 🔍 2. Why Do We Test Security?
- 🧰 3. Types of Tests
- ✅ Vulnerability Assessment
- ✅ Penetration Testing (Pen Test)
- ✅ Security Audit
- ✅ Security Assessment
- ✅ Log Review
- 🧠 4. Testing Methods
- 👨🔧 5. Security Processes to Review
- 📊 6. Test Data Handling
- 📋 7. Reporting Results
- 📈 8. Continuous Monitoring
- ⚠️ 9. Common Tools and Techniques
- Synthetic Monitoring:
- SAST (Static Application Security Testing):
- Black Box vs. White Box Testing:
- Dynamic Testing vs. Static Testing:
- Fuzz Testing:
- Domain 7: Security Operations
- 🛡️ 1. What Is Security Operations?
- 📆 2. Operational Activities
- 🚨 3. Incident Response
- 🔁 4. Business Continuity & Disaster Recovery
- Important Metrics:
- 🏷️ 5. Digital Forensics
- 🔐 6. Security Concepts in Operations
- 👥 7. Personnel Security
- 🔧 8. Resource Protection
- 🧪 9. Testing Controls
- 🛰️ 10. SIEM and Monitoring
- 🧯 11. Fire Prevention & Safety
- CISSP Domain 8: Software Development Security
- 💻 1. What Is Software Development Security?
- 🧱 2. Software Development Life Cycle (SDLC)
- 🧪 3. Software Testing Types
- 🔐 4. Common Software Flaws
- 🛑 5. Secure Coding Practices
- 👥 6. Development Roles
- 🔁 7. Change & Version Control
- 📜 8. Software Security Models & Concepts
- 🔧 9. Software Development Methods
- 📥 10. Third-Party & Open-Source Software
- ⚙️ 11. Deployment & Secure Environments
CIA
The CIA Triad is the foundation of information security, ensuring that data is:
- Confidentiality – Protecting information from unauthorized access.
- Integrity – Ensuring data is accurate and unaltered.
- Availability – Ensuring information and systems are accessible when needed.
Additional Security Properties
- Authenticity (Authentication) – Verifying the identity of users, systems, or data sources to prevent unauthorized access.
- Accountability – Ensuring that actions can be traced to an individual or system through auditing and logging.
- Non-repudiation – Preventing entities from denying their actions by using cryptographic mechanisms like digital signatures and log records.
These additional properties strengthen the CIA Triad and are essential for comprehensive security in CISSP and other cybersecurity frameworks.
CISSP Domain 1_ Security and Risk Management.pdf
✅ CISSP Domain 1 – Security and Risk Management (Simple Notes)
🔒 1. CIA Triad (Main Goals of Security)
- Confidentiality – Keep data private (only the right people can see it).
- Integrity – Keep data correct and unchanged (no one messes with it).
- Availability – Keep systems and data working when needed.
🏛️ 2. Security Rules and Leadership (Governance)
- Security Governance – Leaders making sure security is planned and followed.
- Compliance – Following rules and laws (like GDPR or HIPAA).
- Due Care – Doing what’s expected to keep things safe.
- Due Diligence – Checking regularly to keep things safe.
⚖️ 3. Laws and Rules
- Civil Law – Deals with private issues (e.g., someone sues you).
- Criminal Law – Deals with crimes (e.g., hacking).
- Administrative Law – Government rules (e.g., health data rules).
- Privacy Laws – Protect personal data (like GDPR in Europe).
- Intellectual Property (IP) – Protects creative work (books, logos, inventions).
⚠️ 4. Risk Management
- Risk – Chance of something bad happening.
- How to Handle Risk:
- Avoid – Don’t do the risky thing.
- Reduce – Make it less risky.
- Transfer – Give risk to someone else (like insurance).
- Accept – Know the risk and live with it.
- Risk Analysis:
- Qualitative – Use scores (like high, medium, low).
- Quantitative – Use numbers and money values.
👥 5. Security Job Roles
- Data Owner – Decides who can use data.
- Data Custodian – Takes care of the data.
- User – Follows rules and uses data properly.
- Security Admin – Sets up and watches over security tools.
📄 6. Security Documents
- Policy – Big-picture rules everyone must follow.
- Standard – Specific rules (must follow).
- Guideline – Helpful advice (not required).
- Procedure – Step-by-step instructions.
🚨 7. Business Continuity and Disaster Recovery
- BCP (Business Continuity Plan) – Plan to keep working after a problem.
- DRP (Disaster Recovery Plan) – Plan to fix tech systems after a problem.
- Important Terms:
- RTO (Recovery Time Objective) – How fast you need to recover.
- RPO (Recovery Point Objective) – How much data you can afford to lose.
- Testing the Plan: Practice through different types of tests (paper test, real test, etc.).
🔍 8. Threat Modeling and Controls
- Threat Modeling – Finding out what can go wrong before it does.
- Example: STRIDE (helps find different types of threats).
- Types of Controls:
- Administrative – Policies, training.
- Technical – Firewalls, passwords, encryption.
- Physical – Locks, cameras, guards.
- Control Functions:
- Preventive – Stops problems.
- Detective – Finds problems.
- Corrective – Fixes problems.
- Deterrent – Discourages attacks.
- Compensating – Backup plan.
- Recovery – Gets things back to normal.
🤝 9. Ethics and Good Behavior
- (ISC)² Code of Ethics:
- Help society and protect people.
- Be honest and fair.
- Do your job well.
- Support the cybersecurity profession.
CISSP Domain 2: Asset Security

📦 1. What Are Assets?
- Assets are anything valuable to a company (like data, devices, software, people).
- Goal: Keep assets safe, private, and available.
🗂️ 2. Classifying Information
- Helps you know how important or sensitive data is.
- Steps:
- Find the data (what exists?).
- Classify it (how sensitive is it?).
- Label it (put labels like “Public”, “Internal”, “Confidential”, “Secret”).
- Protect it (use proper controls).
- Common Classification Levels:
- For business: Public → Internal → Confidential → Restricted.
- For government: Unclassified → Confidential → Secret → Top Secret.
🧑💼 3. Roles Related to Data
- Owner – Decides who can access the data.
- Custodian – Takes care of the data (e.g., backups).
- User – Uses data and follows rules.
- Data Controller – Responsible for following privacy laws.
- Data Processor – Works on data for the controller (e.g., cloud provider).
🔐 4. Protecting Data
- In Transit – Data moving over a network (protect using VPN, SSL).
- At Rest – Data stored on disk (use encryption, access control).
- In Use – Data being used in memory or CPU (limit access, clean memory after use).
🔄 5. Data Lifecycle
- Create – Make new data.
- Store – Save the data.
- Use – Access and work with it.
- Share – Send or give access to others.
- Archive – Store long-term (not used often).
- Destroy – Safely delete when no longer needed.
🧨 6. Destroying Data Securely
- Wiping – Overwrite data with random info.
- Degaussing – Use magnets to erase data (for tapes/disks).
- Shredding – Physically destroy the device.
- Purging – Deep clean to remove all data.
🔒 7. Access Control Principles
- Need to Know – Only give access if someone really needs it.
- Least Privilege – Only give the minimum access needed to do a job.
- Separation of Duties – Split responsibilities so one person can’t do everything.
- Mandatory Access Control (MAC) – Access based on rules and labels.
- Discretionary Access Control (DAC) – Owner decides who can access.
- Role-Based Access Control (RBAC) – Access based on job role.
🔎 8. Data Privacy
- Personal data must be protected.
- Follow laws like GDPR (Europe), HIPAA (USA).
- Important terms:
- PII – Personally Identifiable Information.
- Masking – Hiding part of data (e.g., 1234-5678).
- Anonymization – Removing identity completely.
- Pseudonymization – Replacing names with fake ones.
Domain 3: Security Architecture and Engineering
🧱 1. Security Architecture Basics
- It’s how we design, build, and manage secure systems.
- Think of it like the blueprint for a secure building.
🛡️ 2. Security Models (How Security Works in a System)
-
Bell-LaPadula (BLP) – Protects confidentiality.
- No Read Up, No Write Down.
- Example: A secret-level user can’t read top-secret files.
-
Biba Model – Protects integrity.
- No Write Up, No Read Down.
- Example: A low-level user can’t change high-level data.
-
Clark-Wilson – Focuses on data integrity using rules and roles.
-
Brewer-Nash (Coca-Cola Model) – Prevents conflicts of interest.
- Users can’t access competing company data.
-
Bell-LaPadula = Confidentiality
Biba = Integrity
🏗️ 3. Security Architecture Concepts
- Defense in Depth – Use multiple layers of security (firewall + antivirus + monitoring).
- Security Domains – Separated areas with their own rules (e.g., admin network vs. guest network).
- Trusted Computing Base (TCB) – Part of a system you must trust to be secure.
- Security Perimeter – Boundary where the TCB ends.
🧠 4. System Security Concepts
- Process Isolation – One program can’t affect another.
- Memory Protection – Stop programs from reading other program’s memory.
- Virtual Memory – Treat physical memory and disk as one.
- Reference Monitor – Always checks if a user is allowed to access something.
- Security Kernel – The part of the OS that enforces the rules.
🧰 5. Security Capabilities of Systems
- Trusted Platform Module (TPM) – Chip that stores encryption keys securely.
- Hardware Security Module (HSM) – Separate device for handling cryptographic keys.
- Full Disk Encryption – Encrypts all data on a disk (e.g., BitLocker).
- Secure Boot – Makes sure the system starts only with trusted software.
🧪 6. System Evaluation Methods
- Common Criteria (ISO 15408) – Global standard for evaluating security.
- EAL1–EAL7 – Evaluation Assurance Levels (EAL7 = highest assurance).
- TCSEC (Orange Book) – U.S. standard, focuses on confidentiality.
- ITSEC – European standard (focuses on confidentiality, integrity, and availability).
⚙️ 7. Cryptography Basics (More in Domain 4)
- Supports Confidentiality, Integrity, Authentication, and Non-repudiation.
- Common Tools: Hashing, Symmetric/Asymmetric Encryption, Digital Signatures.
🌍 8. Physical Security Controls
- Types:
- Deterrent – Makes attackers think twice (e.g., signs, lights).
- Preventive – Stops access (e.g., locks, fences).
- Detective – Finds intrusions (e.g., cameras, alarms).
- Corrective – Fixes problems after they happen (e.g., fire extinguishers).
- Compensating – Backup controls (e.g., guard if lock fails)
Biba Model
The Biba Model is a security model that protects data integrity (making sure data is not changed in an unsafe way). It follows two simple rules:
- No-Read-Down → You can’t read data from a lower (less trustworthy) level.
- Example: A high-level bank manager can’t read data from an unverified source to avoid bad information.
- No-Write-Up → You can’t write data to a higher (more trustworthy) level.
- Example: A normal employee can’t change critical financial records to prevent mistakes or fraud.
This model is used in banks, government systems, and security software to keep important data safe from corruption.
Brewer-Nash Model
The Brewer-Nash Model, also called the Chinese Wall Model, is a security model designed to prevent conflicts of interest in industries like finance, law, and consulting.
How It Works
The model blocks access to data that could create a conflict of interest. It does this by grouping data into conflict of interest classes (COI).
Two Main Rules:
- No-Read-Conflict:
- If a user (e.g., an analyst) accesses data from one company, they can’t read data from a competing company in the same group.
- Example: If a financial analyst sees data from Company A, they can’t read data from Company B, which is a competitor.
- No-Write-Conflict:
- A user can’t write data that could cause a conflict of interest.
- Example: If an analyst worked with Company A, they can’t provide reports for Company B, ensuring fairness.
Why is it Important?
- Prevents insider trading and biased decision-making.
- Used in banks, investment firms, and legal offices to ensure ethical practices.
Clark-Wilson Security Model
The Clark-Wilson Security Model is a security framework focused on data integrity in business and financial systems. It ensures that only authorized users can modify data in a controlled way.
Key Principles:
- Well-formed Transactions
- Users can’t directly change important data. Instead, they must go through approved procedures (like a banking system that requires multiple steps for a transaction).
- Separation of Duties
- No single person has complete control over a critical process.
- Example: One employee enters financial data, while another approves it.
- Access Control Based on Roles
- Users get access only to what they need for their job.
- Example: A cashier can update sales records, but only a manager can approve refunds.
Why is it Important?
- Prevents fraud, errors, and unauthorized changes.
- Used in banks, financial institutions, and enterprise systems where data accuracy is critical.
Graham-Denning Security Model
This model focuses on secure access control by defining how subjects (users/processes) interact with objects (files, resources) in a system.
Key Idea:
The model describes eight rules (operations) that control how subjects create, delete, and manage objects and other subjects.
The 8 Rules of Graham-Denning Model:
- Create Object – A user can create a new file or resource.
- Delete Object – A user can remove a file or resource.
- Create Subject – A new user/process can be created.
- Delete Subject – A user/process can be removed.
- Read Access – A subject can read an object’s data.
- Write Access – A subject can modify an object’s data.
- Grant Access Rights – A subject can give another subject permissions.
- Delete Access Rights – A subject can take away another subject’s permissions.
Why is it Important?
- Provides a structured way to manage permissions in a system.
- Helps in preventing unauthorized access and maintaining security.
- Used in operating systems, databases, and secure computing environments.
Encryption
Definitions:
- Cryptography: The practice and study of techniques for secure communication to prevent unauthorized access. It ensures data confidentiality, integrity, authentication, and non-repudiation.
- Encryption: The process of converting readable information (plaintext) into a coded form (ciphertext) to prevent unauthorized access.
- Decryption: The reverse of encryption, converting ciphertext back to plaintext.
- Cipher: A pair of algorithms for encryption and decryption, controlled by a key.
- Key: A secret string of characters used to encrypt and decrypt information.
- Symmetric Cryptography: Uses the same key for both encryption and decryption; faster but less secure for large systems.
- Asymmetric Cryptography: Uses a public key for encryption and a private key for decryption; more secure but slower.
- Hashing: A method to convert data into a fixed-length string (hash value) that is difficult to reverse, often used for data integrity.
- Cryptanalysis: The study of techniques to break encryption and decode messages without access to the key.
Summary of Key Topics:
- Cryptography Basics: Originally focused on converting plaintext to ciphertext for secrecy. Modern cryptography addresses confidentiality, integrity, authenticity, and non-repudiation.
- Symmetric vs. Asymmetric Cryptography: Symmetric uses a single shared key, while asymmetric uses paired public and private keys. Asymmetric is more secure for large-scale communication.
- Hashing: Used for data integrity and authentication. Unlike encryption, hashing is one-way and irreversible.
- Cryptanalysis: Attempts to break encryption methods. Includes techniques like frequency analysis and side-channel attacks.
- Data Protection: Data can be protected while at rest (stored) or in transit (being transmitted). Both can use encryption to ensure security.
Main Points:
- Cryptography aims to secure data and communication.
- Encryption and decryption are core processes.
- Symmetric encryption is faster but requires key management.
- Asymmetric encryption is more secure for large systems.
- Hashing is used to verify data integrity, not for encryption.
- Cryptanalysis challenges encryption methods to find vulnerabilities.
- Data protection includes securing data at rest and in transit.
Caesar Cipher
Replacing the actual letter with ciphertext to make encrypted letter.

Encoding and Decoding
- Encoding: Changing information into a different format for easy transmission or storage. It’s not for security, just for compatibility.
- Example: Turning text into Morse code so it can be sent through radio signals.
- Decoding: Changing the encoded message back to its original form.
- Example: Translating Morse code back into text.
Transposition in Cryptography
- What it is: Rearranging the order of characters in the plaintext to create the ciphertext. Unlike substitution, it doesn’t change the actual characters—just their positions.
- Example: If the message is “HELLO”, a transposition might rearrange it to “LOLEH”.
- Purpose: To make the message harder to understand without the correct key.
In simple terms, transposition is like shuffling a deck of cards—the cards (characters) stay the same, but their order changes.
Confusion
- What it means: Making the link between the key and the coded message hard to understand.
- Why it matters: If someone tries to guess the key, they should struggle because the coded message looks too mixed up.
- Example: Imagine mixing paint colors. Once you add many colors, it’s hard to tell which one caused a specific shade.
Diffusion
- What it means: Spreading the impact of each part of the message across the whole coded message.
- Why it matters: It hides patterns, making it harder to guess the original message.
- Example: If you spill ink on a page, it spreads out. The more it spreads, the harder it is to see the original letters.
In Short:
- Confusion = Making it hard to guess the key.
- Diffusion = Hiding patterns in the message.
Key Clustering
- What it is: A situation in cryptography where two different keys generate the same ciphertext from the same plaintext.
- Why it’s a problem: It weakens encryption because finding one of the keys can help guess the other, reducing security.
- Example: Imagine two different keys 1234 and 5678 that, when used to encrypt the word “SECRET”, both give the same result “X1B3Z7”. This overlap is key clustering.
In short: Key clustering is like having two different locks that can be opened by the same key — it’s not supposed to happen and can make things less secure.
Synchronous and Asynchronous in Cryptography
1. Synchronous (Symmetric) Encryption:
- What it is: Uses the same key to encrypt and decrypt data.
- How it works: The sender and receiver must both have the same key, which must be kept secret.
- Example: AES (Advanced Encryption Standard)
- Analogy: Like having the same key for locking and unlocking a door. Both people need the same key.
- Pros: Fast and efficient for large amounts of data.
- Cons: The key must be shared securely, which can be challenging.
2. Asynchronous (Asymmetric) Encryption:
- What it is: Uses two keys — a public key for encryption and a private key for decryption.
- How it works: The public key is shared openly, but the private key is kept secret by the receiver.
- Example: RSA (Rivest-Shamir-Adleman)
- Analogy: Like a mailbox — anyone can put a letter (encrypt) inside using the public key, but only the owner with the private key can take it out (decrypt).
- Pros: No need to share the private key, making it more secure for key exchange.
- Cons: Slower and more resource-intensive than symmetric encryption.
In Short:
- Synchronous (Symmetric) = Same Key — Fast, but secure key sharing needed.
- Asynchronous (Asymmetric) = Public & Private Keys — More secure, but slower.
1. Certificate Authority (CA)
- What it does: Issues digital certificates to verify identities online.
- Why it matters: Ensures secure communication by confirming that websites or users are genuine.
- Example: When you see “https://” on a website, a CA has verified its identity.
2. Registration Authority (RA)
- What it does: Helps the CA verify a user’s identity before issuing a certificate.
- Role: Acts as a middleman to ensure accurate information before certificate approval.
3. Work Factor in Cryptography
- What it means: The time, effort, and resources needed to break an encryption.
- Purpose: Measures the strength of an encryption method. The higher the work factor, the more secure it is.
4. Methods of Cryptography
a. Stream Cipher:
- How it works: Encrypts data one bit or byte at a time.
- Example: RC4 (now considered insecure)
- Fast and suitable for: Real-time communication like voice calls.
b. Block Cipher:
- How it works: Encrypts data in fixed-size blocks (like 64 bits or 128 bits).
- Example: AES (Advanced Encryption Standard)
- Secure and suitable for: Large data files and storage.
5. Initialization Vector (IV)
- What it is: A random value added to the plaintext before encryption.
- Why needed: Ensures the same plaintext doesn’t produce the same ciphertext, increasing security.
- Example: Like adding a random “salt” to a password to make it unique.
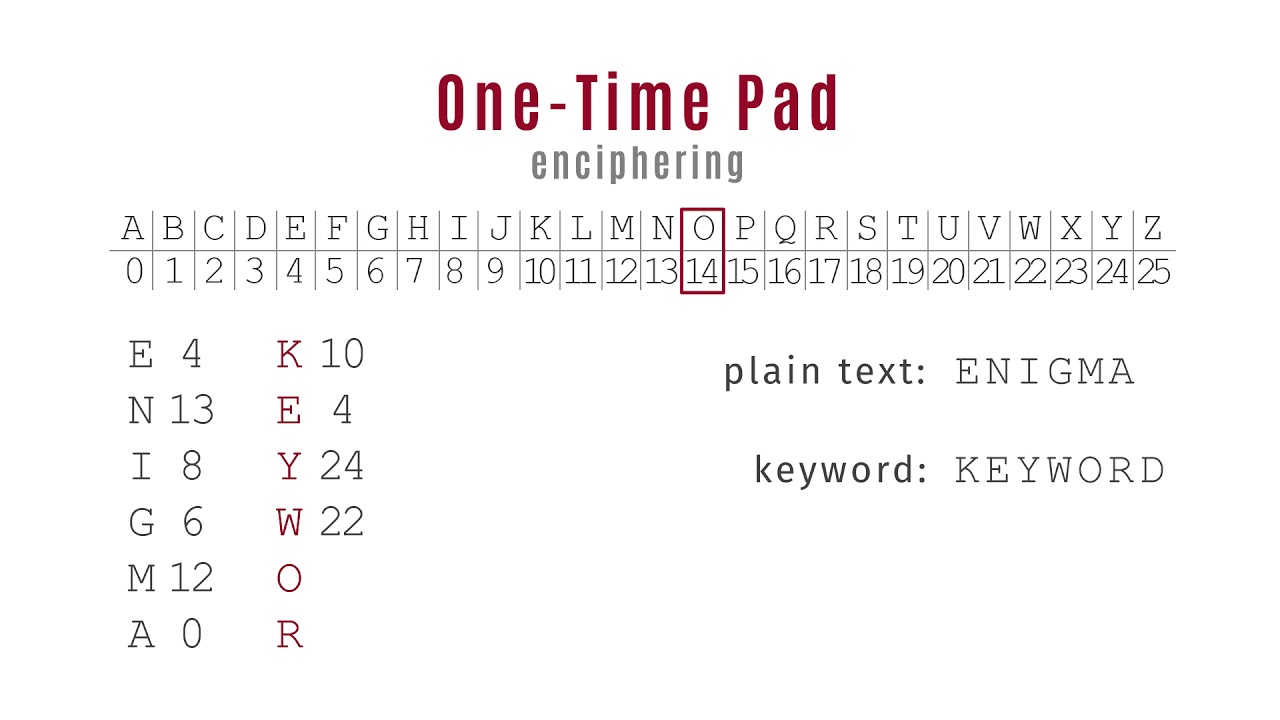
6. One-Time Pad
- What it is: An encryption method using a random, secret key as long as the message itself.
- Why secure: If used correctly (never reused), it’s unbreakable.
- Challenge: The key must be as long as the message and kept completely secret.
7. Steganography
- What it is: Hiding a message inside something else, like an image or audio file.
- Purpose: To keep the existence of the message a secret.
- Example: Hiding text in the color data of an image file.
8. ECB vs. CBC (Modes of Block Cipher)
- ECB (Electronic Codebook):
- How it works: Encrypts each block of plaintext separately.
- Problem: Identical plaintext blocks create identical ciphertext, revealing patterns.
- Example: Like stamping the same seal on each page — easy to spot duplicates.
- CBC (Cipher Block Chaining):
- How it works: Each plaintext block is XORed with the previous ciphertext block before encryption.
- Benefit: Hides patterns; more secure than ECB.
- Example: Like linking a chain — each link (block) depends on the previous one.
Stream vs. Block Ciphers:
- Stream Cipher: Encrypts data bit by bit or byte by byte. Faster and ideal for real-time data like voice or video.
- Example: RC4 (now considered insecure)
- Block Cipher: Encrypts data in fixed-size blocks (e.g., 64 or 128 bits). More secure and commonly used for file encryption.
- Example: AES (Advanced Encryption Standard)
Block Cipher Modes of Operation:
1. CFB (Cipher Feedback Mode):
- How it works: Uses an Initialization Vector (IV). Encrypts small segments (like stream ciphers) using a block cipher.
- Purpose: Good for streaming data, like network communications.
- Example: Like a relay race — each runner (block) relies on the previous one.
2. OFB (Output Feedback Mode):
- How it works: The block cipher output is fed back into the encryption process, creating a stream of random bits. The IV and key generate this stream.
- Purpose: Good for noisy channels, as errors don’t spread.
- Example: Like a playlist on repeat — the same track (key stream) plays repeatedly.
3. CTR (Counter Mode):
- How it works: Uses a counter that increments with each block. The counter is combined with the key to create a unique keystream.
- Purpose: Fast and can encrypt multiple blocks simultaneously. Widely used for parallel processing.
- Example: Like numbered pages — each page (block) has a unique number (counter).
In Short:
- CFB: Feeds previous ciphertext into the encryption.
- OFB: Feeds the block cipher’s output to create a key stream.
- CTR: Uses a counter to generate a unique key stream for each block.
These modes help block ciphers work like stream ciphers, offering flexibility and better security in different situations.
Cryptography Algorithms: Quick and Easy Notes
1. Data Encryption Standard (DES)
- What it is: An older symmetric encryption method that uses a 56-bit key.
- Weakness: Vulnerable to brute-force attacks due to short key length.
- Replaced by: AES (Advanced Encryption Standard) for stronger security.
2. AES (Advanced Encryption Standard)
- What it is: A symmetric encryption method and the current standard for secure encryption.
- Key Sizes: 128-bit, 192-bit, 256-bit (longer keys = stronger security).
- Usage: Used in Wi-Fi (WPA2), VPNs, and secure communication.
- Fast, strong, and widely trusted.
3. SAFER (Secure and Fast Encryption Routine)
- Where it’s used: In Bluetooth encryption for secure data transfer.
- Design: Made to resist known attacks, fast for real-time communication.
- Focus: Lightweight yet secure, suitable for devices with limited resources.
4. RSA (Rivest-Shamir-Adleman)
- What it is: An asymmetric encryption method using two keys — public (encrypt) and private (decrypt).
- Security: Based on the difficulty of factoring large prime numbers.
- Usage: Secure data exchange over the internet (like HTTPS).
- Example: Public key encrypts a message; private key decrypts it.
5. Diffie-Hellman Algorithm
- What it does: A method for secure key exchange over an insecure network.
- Use Case: Establishes a shared secret key without directly sharing it.
- Vulnerability: If not combined with authentication, it can be vulnerable to “Man-in-the-Middle” attacks.
- Example: Alice and Bob agree on a shared key without others knowing it.
6. ElGamal Algorithm
- What it is: An asymmetric encryption method based on the Diffie-Hellman principle.
- Features: Used for digital signatures and encryption.
- Stronger but slower compared to RSA.
- Example: Common in digital certificates and secure communication.
7. ECC (Elliptic Curve Cryptography)
- What it is: An asymmetric encryption method that uses elliptic curves for encryption.
- Benefit: Provides strong security with shorter keys, making it faster and efficient.
- Use Case: Common in mobile devices and secure messaging.
- Example: A 256-bit ECC key is as strong as a 3072-bit RSA key.
8. Birthday Paradox/Birthday Attack
- What it is: A probability theory showing that in a group of 23 people, there’s a high chance two share a birthday.
- In cryptography: Used to find collisions (two inputs producing the same hash value) in hash functions.
- Risk: If a hash function is weak, attackers can find two different messages with the same hash.
- Example: Breaking MD5 through collision attacks.
In Short:
- DES: Old and weak.
- AES: Strong and modern.
- SAFER: Used in Bluetooth.
- RSA: Asymmetric, public/private key.
- Diffie-Hellman: Key exchange.
- ElGamal: Secure but slower.
- ECC: Strong, fast, and efficient.
- Birthday Attack: Exploits hash collisions.
These notes should help you quickly understand these essential cryptography concepts!
- Linear Cryptanalysis:
- Finds linear relationships between plaintext, ciphertext, and key.
- Used to approximate encryption behavior.
- Chosen Plaintext Attack:
- Attacker selects plaintexts and observes ciphertexts.
- Aims to find encryption keys.
- Differential Cryptanalysis:
- Analyzes how changes in plaintext affect ciphertext.
- Effective for block ciphers.
- Implementation Attacks: Exploit weaknesses in the implementation, not the algorithm itself.
- Side Channel Attack: Uses physical data like power, timing.
- Fault Analysis: Induces errors to extract key info.
- Probing Attack: Physically accesses internal data paths.
- Replay Attack: Captures and reuses valid data for unauthorized access.
Domain 4: Communication and Network Security
OSI Layers (Open Systems Interconnection Model)
The OSI model is a conceptual framework that standardizes network communication. It has 7 layers, each serving a specific function in data transmission:
- Physical Layer (Layer 1): Deals with hardware transmission like cables and signals.
- Data Link Layer (Layer 2): Manages data frames between devices. Uses MAC addresses.(Frames)
- Network Layer (Layer 3): Handles routing and logical addressing (IP addresses).
- Transport Layer (Layer 4): Ensures reliable data transfer using protocols like TCP and UDP.
- Session Layer (Layer 5): Manages sessions and connections.
- Presentation Layer (Layer 6): Transforms data formats (encryption, compression).
- Application Layer (Layer 7): Interface for end-user applications (HTTP, FTP).
CSMA (Carrier Sense Multiple Access)
- Definition: A network protocol that checks if a communication channel is clear before transmitting data.
- OSI Layer: Works at the Data Link Layer (Layer 2).
- Types:
- CSMA/CD (Collision Detection): Used in Ethernet to detect collisions.
- CSMA/CA (Collision Avoidance): Used in Wi-Fi networks to avoid collisions.
Ethernet (IEEE 802.3)
- Definition: A set of networking technologies for wired LANs (Local Area Networks). Uses frames for data transmission.
- OSI Layer: Operates at Layer 1 (Physical) and Layer 2 (Data Link).
- Speed: Supports speeds from 10 Mbps to 400 Gbps.
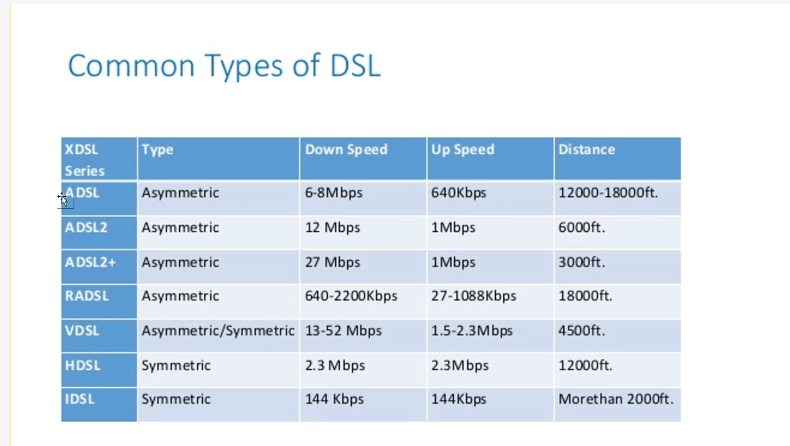
ADSL (Asymmetric Digital Subscriber Line)
- Definition: A type of DSL technology that provides faster download speeds than upload speeds, typically used for internet access over telephone lines.
- OSI Layer: Operates mainly at the Physical Layer (Layer 1).
- Speed: Download speeds up to 24 Mbps, upload speeds up to 1.4 Mbps.
RADSL (Rate-Adaptive Digital Subscriber Line)
- Definition: A variation of ADSL that automatically adjusts transmission rates based on line conditions.
- OSI Layer: Works at the Physical Layer (Layer 1).
- Feature: Dynamic speed adjustment improves stability over long distances.
VDSL (Very High Bitrate Digital Subscriber Line)
- Definition: An advanced DSL technology offering much higher speeds than ADSL.
- OSI Layer: Operates at the Physical Layer (Layer 1).
- Speed: Supports download speeds up to 300 Mbps and upload speeds up to 100 Mbps over short distances.
→ ARP (Address Resolution Protocol)
is used to map IP addresses to MAC addresses within a local network, enabling devices to communicate effectively by translating logical IP addresses to physical MAC addresses.
→ MPLS (Multiprotocol Label Switching)
is a network technology that uses labels to efficiently route data packets, improving traffic management and ensuring faster, more reliable data transmission, particularly for applications requiring low latency and predictable performance.
ICMP (Internet Control Message Protocol)
A network layer protocol used for error reporting and diagnostic functions. It helps network devices like routers and hosts communicate issues like unreachable destinations or timeouts.
Examples:
- When you use the ping command, ICMP is used to check if a device is reachable.
- ICMP messages help detect network congestion or misconfigurations.
- ICMP can report if a packet’s TTL (Time to Live) has expired.
IGMP (Internet Group Management Protocol)
A communication protocol used for managing multicast group memberships in IPv4 networks. It allows devices to join or leave multicast groups.
Examples:
- A router uses IGMP to check if there are devices interested in a specific multicast stream.
- Streaming services use IGMP to deliver content to multiple users efficiently.
- IGMP Snooping helps switches optimize multicast traffic.
OSPF (Open Shortest Path First)
A routing protocol used to find the best path for data within an IP network. It operates within a single Autonomous System (AS) and uses the Dijkstra algorithm.
Examples:
- OSPF quickly adjusts routing tables when network changes occur.
- It’s commonly used in large enterprise networks.
- OSPF divides networks into areas to optimize routing.
SNMP (Simple Network Management Protocol)
A protocol used to monitor, manage, and configure network devices like routers, switches, servers, and printers. It uses a centralized manager to collect data from devices using agents.
Examples:
- Network administrators use SNMP to monitor device performance.
- SNMP can trigger alerts if a device fails or exceeds usage thresholds.
- SNMPv3 includes enhanced security features like authentication and encryption.
LDAP (Lightweight Directory Access Protocol)
A protocol used to access and maintain distributed directory information services over an IP network. It’s often used for centralized authentication.
Examples:
- LDAP is used to authenticate users in Active Directory environments.
- Email servers use LDAP to find user information like email addresses.
- LDAP can integrate with Single Sign-On (SSO) for secure access control.
SDN (Software-Defined Networking)
A networking approach that separates the control plane (decision-making) from the data plane (traffic forwarding). This allows centralized, programmable network management using software applications, making networks more flexible and easier to manage.
Examples:
- SDN controllers can dynamically adjust network traffic based on changing conditions.
- Cloud providers use SDN to manage virtual networks across data centers.
- SDN simplifies network management by enabling centralized monitoring and automation.
CDN (Content Delivery Network)
A distributed network of servers that deliver web content to users based on their geographic location. CDNs improve website speed, reduce latency, and enhance the user experience by caching content closer to the end-users.
Examples:
- Streaming platforms use CDNs to deliver videos smoothly worldwide.
- A CDN helps reduce website loading time for users far from the origin server.
- CDNs protect against DDoS attacks by distributing traffic across multiple servers.
PAT (Port Address Translation)
A type of NAT (Network Address Translation) that allows multiple devices on a local network to share a single public IP address by mapping each device’s connection to a unique port number. It is also known as NAT Overload.
Examples:
- PAT lets multiple devices in a home network access the internet using a single public IP address.
- When you browse the internet from multiple devices on the same network, PAT assigns unique port numbers to each session.
- PAT helps conserve public IPv4 addresses and provides a layer of security by hiding internal IP addresses.
SIP (Session Initiation Protocol)
A signaling protocol used to establish, maintain, modify, and terminate real-time communication sessions, such as voice calls, video conferences, and messaging over IP networks. It operates mainly at the Application Layer of the OSI model.
Examples:
- SIP is used to initiate and end VoIP (Voice over IP) calls.
- Video conferencing platforms use SIP to set up multimedia sessions between participants.
- SIP works alongside protocols like RTP (Real-Time Protocol) to transmit voice and video data.
IRC (Internet Relay Chat)
A text-based communication protocol used for real-time chatting over the internet. It enables users to join channels (chat rooms) or have private conversations. IRC was widely popular before modern messaging apps.
Examples:
- Developers use IRC channels to discuss open-source projects and collaborate.
- Some gaming communities still use IRC for real-time communication.
- IRC networks can be accessed using dedicated clients like mIRC or HexChat.
Domain 5: Identity and Access Management
Centralized vs. Decentralized vs. Hybrid
- Centralized: Access control decisions are managed by a single authority, offering consistent policies but prone to single points of failure.
- Decentralized: Decisions are distributed across multiple authorities, increasing flexibility but complicating policy enforcement.
- Hybrid: Combines centralized and decentralized approaches, balancing control and flexibility.
Access Control Management
Processes and technologies used to grant, restrict, and monitor access to resources based on policies. It ensures users have appropriate access levels and maintains system security.
Physical Access Control Systems (PACS)
Security systems that control physical entry to facilities using devices like card readers, biometric scanners, and surveillance. Examples: keypads, turnstiles.
Access Control Token
Physical or digital devices (cards, fobs, software tokens) used to authenticate and authorize user access. Can include One-Time Passwords (OTPs) for enhanced security.
Provisioning and Deprovisioning
- Provisioning: Granting access rights and resources to users during onboarding.
- Deprovisioning: Revoking access when a user leaves or changes roles to maintain security.
Biometrics
Authentication methods using unique physical or behavioral traits like fingerprints, iris scans, voice recognition. Offers strong security but raises privacy concerns.
FIM (Federated Identity Management)
Allows a user to access multiple systems across different domains using a single identity. Reduces the need for multiple credentials.
SAML (Security Assertion Markup Language)
An XML-based protocol for authentication and authorization data exchange. Commonly used for Single Sign-On (SSO) in web applications.
OAuth (Open Authorization)
An authorization protocol allowing third-party applications to access resources without sharing user credentials. Commonly used by platforms like Google and Facebook.
OpenID
An authentication protocol that allows users to authenticate with multiple services using a single identity. Often paired with OAuth for combined authentication and authorization.
LDAP (Lightweight Directory Access Protocol)
A protocol used to query and manage directory information, like user data in a network. Commonly used for authentication in corporate environments.
Types of Access Control
- DAC (Discretionary Access Control): Access based on owner’s discretion. Flexible but less secure.
- MAC (Mandatory Access Control): Strict access policies controlled by a central authority. High security, often used in government.
- NDAC (Non-Discretionary Access Control): Access governed by organizational roles rather than individuals.
- RBAC (Role-Based Access Control): Access based on user roles within an organization. Efficient and widely used.
- Rule-Based Access Control: Access decisions based on predefined rules like time or location.
- ABAC (Attribute-Based Access Control): Access based on user, resource, and environmental attributes. Offers fine-grained control.
Accountability in Identity and Access Management (IAM)
Ensures users are responsible for their actions by maintaining logs, audits, and monitoring activities. Crucial for compliance and incident response.
Domain 6: Security Assessment and Testing
🧪 1. What Is Security Assessment & Testing?
- It’s about checking if security controls are working.
- Goal: Find weaknesses before attackers do.
🔍 2. Why Do We Test Security?
- To make sure systems are secure, working properly, and meeting policies.
- Helps you find:
- Misconfigurations
- Vulnerabilities
- Gaps in access control
- Policy violations
🧰 3. Types of Tests
✅ Vulnerability Assessment
- Scan for known issues (like open ports, missing patches).
- Tool Example: Nessus, OpenVAS
✅ Penetration Testing (Pen Test)
- Simulate a real attack to test defenses.
- Follows a step-by-step process:
- Planning – Get approval, set rules.
- Recon – Gather info.
- Scanning – Find weak spots.
- Exploitation – Try to break in.
- Reporting – Share results and fixes.
✅ Security Audit
- A formal review of policies, access, and controls.
- Often done by third parties.
✅ Security Assessment
- A full check of the system’s security, including risk analysis and testing.
✅ Log Review
- Check system logs for signs of trouble or misuse.
🧠 4. Testing Methods
- Manual Testing – Done by a human (more detailed but slower).
- Automated Testing – Tools run tests quickly (but may miss logic issues).
- Code Review – Look at the actual code to find errors or backdoors.
- Static Testing – Test code without running it.
- Dynamic Testing – Test while code is running (like during execution).
- Fuzzing – Send random/bad input to see if the app crashes.
👨🔧 5. Security Processes to Review
- User Access Reviews – Are users still supposed to have access?
- Privilege Audits – Are users given too much power?
- Change Management – Were changes tested and approved?
- Patch Management – Are systems updated?
📊 6. Test Data Handling
- Use fake data (test data) during testing, not real customer data.
- If real data is used, protect it like production.
📋 7. Reporting Results
- Reports should show:
- What was tested
- What was found
- How serious the issues are
- Recommendations to fix them
📈 8. Continuous Monitoring
- Not just one-time testing — you should keep checking over time.
- Use tools like:
- SIEM (Security Info and Event Management)
- IDS/IPS
- Log analyzers
⚠️ 9. Common Tools and Techniques
- Nmap – Network scanner
- Nessus/OpenVAS – Vulnerability scanners
- Metasploit – Exploitation framework
- Burp Suite – Web app testing
- Wireshark – Packet analyzer
- Syslog – For log management
Synthetic Monitoring:
A technique where automated, simulated transactions are used to test the performance and functionality of an application from an end-user perspective.
Example: Companies use synthetic monitoring to check website uptime from various global locations.
SAST (Static Application Security Testing):
A method of analyzing source code for security vulnerabilities without executing the program. It focuses on finding issues early in the development phase.
Example: Developers use SAST tools to identify insecure coding practices during the coding process.
Black Box vs. White Box Testing:
-
Black Box Testing: Testing without any knowledge of the internal code or architecture. Focuses on input-output behavior.
Example: A tester inputs random values into a login form to see if unauthorized access is possible.
-
White Box Testing: Testing with full access to the internal code and logic. Analyzes the internal structures.
Example: A developer checks the flow of logic in a function to ensure there are no vulnerabilities.
Dynamic Testing vs. Static Testing:
-
Dynamic Testing: Executing the code to find errors or bugs during runtime.
Example: Running a program to see if all functions work as expected.
-
Static Testing: Reviewing code, requirements, or documentation without execution.
Example: Conducting a code review to identify syntax errors or potential vulnerabilities.
Fuzz Testing:
An automated testing technique that feeds random or unexpected inputs into a system to discover vulnerabilities or unexpected behaviors.
Example: A security team uses fuzz testing to see if invalid inputs can crash an application.
Domain 7: Security Operations
🛡️ 1. What Is Security Operations?
- It’s about keeping systems secure day-to-day.
- Includes monitoring, responding to incidents, backups, and handling risks.
📆 2. Operational Activities
- Monitoring – Watch systems for threats.
- Logging – Record events (who did what and when).
- Backup & Recovery – Save copies of data in case something goes wrong.
- Patch Management – Keep software updated to fix security holes.
- Configuration Management – Keep track of system settings and changes.
🚨 3. Incident Response
Respond quickly and properly when something bad happens.
- Steps in Incident Handling:
- Preparation – Plan and train before something happens.
- Detection – Spot the issue (from logs, alerts).
- Containment – Stop it from spreading.
- Eradication – Remove the threat.
- Recovery – Get systems back to normal.
- Lessons Learned – Review and improve.
- Use a playbook or runbook to follow a plan.
🔁 4. Business Continuity & Disaster Recovery
- Business Continuity Plan (BCP) – Keep business running during disruption.
- Disaster Recovery Plan (DRP) – Recover IT systems after a disaster.
Important Metrics:
- RPO (Recovery Point Objective) – How much data loss is OK?
- RTO (Recovery Time Objective) – How fast to restore service?
🏷️ 5. Digital Forensics
- Used to collect and analyze evidence after a security incident.
- Must follow chain of custody – keep track of who handled the evidence.
🔐 6. Security Concepts in Operations
- Least Privilege – Users only get what they need.
- Separation of Duties – No one person has full control.
- Job Rotation – People switch roles to avoid fraud.
- Need to Know – Only access if necessary.
👥 7. Personnel Security
- Background checks – Before hiring.
- Security awareness training – Teach staff to stay alert.
- Termination procedures – Remove access quickly when someone leaves.
🔧 8. Resource Protection
- Data classification – Label data (Public, Internal, Confidential, Secret).
- Media protection – Secure storage and disposal of USBs, hard drives, etc.
- Data destruction – Shred, wipe, or degauss before discarding.
🧪 9. Testing Controls
- Tabletop Exercise – Team talks through a simulated incident.
- Drills – Practice emergency procedures.
- Full interruption test – Actually shut systems down (rare and risky).
- Simulation test – Act like a real disaster, without turning things off.
🛰️ 10. SIEM and Monitoring
- SIEM (Security Info and Event Management) – Collects and analyzes logs.
- Helps detect attacks early and alert the team.
- Example tools: Splunk, IBM QRadar, ArcSight.
🧯 11. Fire Prevention & Safety
- Fire suppression systems:
- Water – For regular fires (not good for servers).
- Gas-based (like FM-200) – For data centers.
- Always follow safety procedures to protect people and equipment.
CISSP Domain 8: Software Development Security
💻 1. What Is Software Development Security?
- It’s about making software secure from the beginning.
- Goal: Build apps that are safe, trusted, and hard to hack.
🧱 2. Software Development Life Cycle (SDLC)
SDLC = Steps followed to make software.
Phases:
- Planning – What are we building?
- Design – How will it work?
- Development – Write the code.
- Testing – Check for bugs or security issues.
- Deployment – Release it to users.
- Maintenance – Fix bugs, update as needed.
🛡️ Add security at every step (called Secure SDLC).
🧪 3. Software Testing Types
- Static Testing – Check code without running it (e.g., code review).
- Dynamic Testing – Run the program and test it live.
- Fuzz Testing – Send random data to see if it crashes.
- Regression Testing – Make sure old features still work after changes.
🔐 4. Common Software Flaws
- Buffer Overflow – Too much data crashes memory.
- SQL Injection – Attacker tricks database with code.
- Cross-site Scripting (XSS) – Injects code into a webpage.
- Cross-site Request Forgery (CSRF) – Tricks users into doing things they didn’t mean to.
- Insecure APIs – Weak links between apps.
🛠️ Fix bugs early to avoid bigger problems later.
🛑 5. Secure Coding Practices
- Input Validation – Always check user input.
- Output Encoding – Clean data before showing it.
- Error Handling – Don’t show system details in error messages.
- Principle of Least Privilege – Code runs with minimum access.
- Code Signing – Verify code comes from a trusted source.
👥 6. Development Roles
- Developers – Write and test code.
- Testers – Find bugs or security holes.
- Architects – Design overall structure.
- Security Team – Help secure the software.
Everyone must work together for secure software.
🔁 7. Change & Version Control
- Change Management – Plan and approve software updates.
- Version Control – Track changes in code (e.g., Git).
- Helps teams work better and avoid mistakes.
📜 8. Software Security Models & Concepts
- Trusted Computing Base (TCB) – Core part of the system that must stay secure.
- Security Models (like Bell-LaPadula, Biba) – Rules for access and control.
- Reference Monitor – Always-enforced, always-invoked access control logic.
🔧 9. Software Development Methods
- Waterfall – Step-by-step, one phase at a time.
- Agile – Fast, flexible, small updates.
- DevOps – Dev + Operations working together.
- DevSecOps – Dev + Security + Ops (security built into DevOps process).
📥 10. Third-Party & Open-Source Software
- Must be checked for:
- Malware
- Licensing issues
- Hidden vulnerabilities
- Use tools to scan and monitor open-source components.
⚙️ 11. Deployment & Secure Environments
- Production – Live system users interact with.
- Staging/Test – Used to test before going live.
- Development – Where coding happens.
💡 Never mix testing and production environments!